
This chapter covers network administration techniques for installing, upgrading, and operating Command AntiVirus. These techniques can be combined to support local workstations and off-site users.
For example, you can place Command AntiVirus on the server and then users can install the program to their local hard drives. For more information about this interactive installation, refer to Installing from the Server.
You can also update Command AntiVirus automatically, with no user interaction, to numerous workstations from a server. This process is completed through our Automatic Update feature. For more information about Automatic Update, refer to Automatic Update.
Scanning can also be automated. For example, you can install Command AntiVirus on a server and run a local DOS virus scan when the user logs in. This technique is helpful when workstation drive space is limited or when configuring each workstation separately is inconvenient. To learn more about this scanning technique, refer to Running A DOS Scan At Login.
To provide system protection against new viruses, we update Command AntiVirus frequently. You can download interim releases from our web, FTP and BBS sites. To protect your systems, be sure to keep your copy of Command AntiVirus updated. For more information about installing the program from a downloaded version, refer to Installing Command AntiVirus From the Server.
In addition to providing instructions in how to set up Command AntiVirus for network administration, this chapter also covers some of the additional tools and techniques available to administrators. Some of these tools include:
- Restricting users from disinfecting their workstations.
- Preventing workstations from scanning network drives.
- Using the administrative utility programs and special batch files that come with Command AntiVirus.
- Broadcasting and controlling virus alert broadcast messages.
This method allows each workstation to install Command AntiVirus manually from the server without using any installation diskettes.
There are two special batch files that you can use to simplify the server-based distribution process, NETDISK.BAT and ONEDISK.BAT. After you have set up a shared directory on a network of your choice, both batch files copy the installation files to that directory. Once the files are in place, users can go to this installation directory and run either SETUP or INSTALL to have Command AntiVirus install to their local workstations.
Choose NETDISK.BAT if you are working from the installation diskettes you have received from Command Software. Choose ONEDISK.BAT if you have downloaded a version from our BBS or FTP site.
NETDISK.BAT is on the installation diskettes that you have received from Command Software.
 |
NOTE: You must run NETDISK.BAT from the server. By doing so, the files needed for server-to-workstation installation can be copied to a shared directory. |
To use NETDISK, follow these steps:
- Create a shared F-PROT directory on the server and then change to that directory.
- Insert Command AntiVirus Installation Disk #1 into drive A of your workstation or server.
- Copy NETDISK.BAT from drive A to the shared directory that you created in Step 1.
- From within the shared directory, type the following command:
NETDISK A:- Press Enter. The system displays a brief instructional screen.
- When you have finished reading the instructions, press Enter to continue.
- Insert Command AntiVirus Installation Disk#1 into drive A.
- Follow the screen instructions. When the copying is complete, any user with access to the shared directory that you created in Step 1 can run INSTALL from DOS or SETUP from Windows to perform a standard installation of Command AntiVirus from the server to the user's local hard drive.
Although ONEDISK.BAT is similar to NETDISK.BAT, you use ONEDISK.BAT with downloaded versions of Command AntiVirus, not with installation diskettes.
If you download Command AntiVirus, you will receive a large executable file.
To use this file, you need to place it in a separate, temporary directory and run it. When you run the downloaded file, it produces several other files, one of which is ONEDISK.BAT.
The following instructions will help you use ONEDISK.BAT. You can also find instructions for using ONEDISK.BAT in INSTALL.DOC, which is contained in the downloaded file.
- Create a shared directory on the server for Command AntiVirus installation files.
- Change to the temporary directory that contains the downloaded files. For example, at the command line type:
CD C:\DOWNLOAD- Press Enter.
- Type ONEDISK followed by the drive and path of the shared directory that you created in Step 1. For example, if you created the directory, F-PROT, in the PUBLIC directory on drive F, at the command line type:
ONEDISK F:\PUBLIC\F-PROT- Press Enter. When the copying is complete, any user with access to the shared directory that you created in Step 1 can run INSTALL from DOS or SETUP from Windows to perform a standard installation of Command AntiVirus to their local hard drive.
For example, from the Start menu in Windows, choose Run. Be sure to specify the path and press Enter. For example:
F:\PUBLIC\F-PROT\SETUP
 |
The default installation automatically places the
following line in your AUTOEXEC.BAT file:
C:\F-PROT\F-PROT /HARD /TODAY |
This command provides for a daily DOS scan of the hard drive. To insure that this daily scan takes place before attaching to the network, make sure that this command is placed before any network calls.
For detailed information about all of the command lines switches that can be used with Command AntiVirus, refer to the Command AntiVirus in DOS chapter.
If you have several workstations, each with a different operating system, you can perform a partial or full-product update of Command AntiVirus on each station directly from a server by using our Automatic Update feature. This feature provides system administrators with the ability to distribute and update the program quickly on multiple workstations in a multi-platform environment with no user interaction.
Automatic Update operates by placing Command AntiVirus files in a unique parent directory in a shared location on the network. When the user starts the computer, the Automatic Updates process compares the dates of the files on the workstation with those on the server. If the server dates are newer, the server responds by automatically updating the workstations with the newer program files.
For example, if only the definition (*.def ) files have changed since the last update, then only those files will be updated. If a new version is available, then the program begins a complete SETUP.
Component updates are not visible to the user. At most, the user may notice that the system is a bit slower. With full-product updates, the system displays the SETUP screens, but no action is required.
 |
NOTE: To use the Automatic Update feature, Command AntiVirus must be installed on each workstation. For new installations, you must run SETUP manually from the workstation. |
The following instructions will help you use the Automatic Update feature:
- In a shared location on the network, create a unique parent directory to store the .DEF and .FPT files. This directory is referred to as the remote setup location. For example:
S:\NEWFPROT- Download and extract the latest definition files and copy them to the remote setup location.
- Create a subdirectory called setup. For example:
S:\NEWFPROT\SETUP- Copy all of the product files into this subdirectory.
 |
NOTE: Copy the files from the product diskettes or from a downloaded copy. Do not use files from the installation directory. |
- Locate the SETUP.INI file and search for: AutoUpdateDir=
- Type in the location of the remote setup location after the equal sign. For example:
AUTOUPDATEDIR=S:\NEWFPROT- Save the changes.
- Open Command AntiVirus.
- Click Options.
- Click Automatic Update. The system displays the Automatic Update dialog box.
- Click Browse. The system displays the Browse Open dialog box.
- Select the drive\path of the remote setup location. For example:
The directory path must point to the remote setup location regardless of whether you are performing partial or full-product updates.S:\NEWFPROT
 |
NOTE: When the drive\path selected is a network drive, the selection is converted to a Universal Naming Convention (UNC) path. |
- Click OK. The Browse Open dialog box closes.
- Click OK. The update occurs automatically when the user restarts the computer or if the user leaves the computer on, between 4 a.m. and 5 a.m.
 |
NOTE: Once you complete this process, workstations are updated automatically each time you place updated files in the remote setup location and setup subdirectory. |
Component updates are not visible. At most, the user may notice that the system is a bit slower. With full-product updates, the system displays the SETUP screens, but the user does not need to take any action.
 |
NOTE: If the updated files require that you restart your system for the changes to take effect, the system displays the following error message: |
"We have updated some files in this release. These files and some settings will not take effect until a reboot is performed. In the interim your system remains fully protected."
As soon as an update takes place, the program does not automatically update again for at least 24 hours. The Update Now button allows the user to update the individual workstation immediately.
 |
There are no restrictions to prevent the user from changing the path of the remote setup location. If the user changes the path, the updates will be made from the path specified. |
 |
NOTE: To turn off the Automatic Update feature, leave the remote setup location blank. |
For more information about the Automatic Update dialog boxes and the Update Now button, refer to Automatic Update located in the Command AntiVirus in Windows chapter.
If you want to run a DOS scan on your workstations at login without actually having the program on the workstations, use the following instructions:
- Install Command AntiVirus on a workstation hard drive. By default, the program files are installed to C:\F-PROT. This process allows you to copy the program files to a shared directory on the server.
- Create a shared F-PROT directory on a server. For example, create an F-PROT directory in the PUBLIC directory on drive F. All users need Read and File Scan rights to this directory.
- Copy all of the program files in the local directory, C:\F-PROT, to the shared directory, F:\PUBLIC\F-PROT, on the server.
- For NetWare 3.1x, modify the LOGIN script with the following four lines. For NetWare 4.x, you must use bindery emulation.
DOS SET FP-DATA="C:\F-PROT.DAT"
\PUBLIC\F-PROT\F-PROT /HARD /TODAY
\PUBLIC\F-PROT\VIRSTOP
\PUBLIC\F-PROT\NOVCAST
 |
NOTE: If you are running Banyan Vines, you can use the
four lines in Step 4 if you replace NOVCAST with BANCAST. For example:
\PUBLIC\F-PROT\BANCAST |
The FP-DATA line is necessary because the daily scan option writes a very small data file that must remain on the local drive (or any drive to which the user has "write" access).
Use LOGIN.COM to reserve a buffer for terminate and stay resident programs (TSRs) that will be run from NetWare's LOGIN.EXE. As soon as the login process is complete, the unused buffered memory areas are available again to the system. This process prevents the fragmentation that normally occurs with LOGIN.EXE.
 |
To use LOGIN.COM, place the file in the same location as your LOGIN.EXE (usually F:\LOGIN). Do not delete LOGIN.EXE. |
In your login script, include a # symbol at the start of the line that loads the TSR. For example:
#C:\F-PROT\VIRSTOP
Many administrators want to restrict their users from increasing the network load with repetitive or unnecessary scans. If a virus is found locally, the administrator may prefer to be notified in order to personally disinfect that workstation.
To help administrators in their efforts to restrict user intervention, Command AntiVirus includes the following specialized utility.
You can use FPWCFG.EXE to modify Command AntiVirus for Windows executable file, F-PROTW.EXE. Modifying F-PROTW.EXE allows administrators to restrict the user's ability to scan network drives, to disinfect viruses, and to disable Dynamic Virus Protection (DVP).
 |
NOTE: To maintain administrator control over these actions, do not make FPWCFG.EXE available to your users. |
After installing Command AntiVirus on the administrator's workstation, use the following instructions to modify FPROTW.EXE:
- Run FPWCFG.EXE (you will find it on the installation diskettes) from within Windows. The system displays the following dialog box appears:
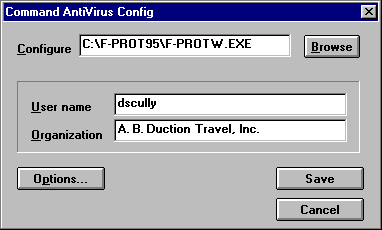
Command AntiVirus Config Dialog Box- Click on Browse and locate F-PROTW.EXE in the F-PROT directory.
- Click on Options.
- Select the Scan Network check box.
- Clear the Allow Disinfection check box.
- Click on Save. The system saves the changes that you made in the Command AntiVirus Config dialog box to the F-PROTW.EXE file.
You can now use the modified F-PROTW.EXE as part of the installation process.
If the users are installing from the server or if you want to change your diskettes, you must first use PKZIP to include the modified F-PROTW.EXE in the existing file, SE_FPRTW.EXE. (SE_FPRTW.EXE is an installation file). For example:
PKZIP SE_FPRTW.EXE F-PROTW.EXE
Command AntiVirus does not include PKZIP. PKZIP is available in many of the major shareware sites on the Internet.
After you have zipped F-PROTW.EXE into SE_FPRTW.EXE, copy the new SE_FPRTW.EXE either to the server's installation directory or to the diskette that will be used for installation. Any future installations that use the modified SE_FRPTW.EXE will contain the restrictions that you added to F-PROTW.EXE.
The following batch files provide options that will simplify the administrator's distribution tasks.
After downloading Command AntiVirus update file, you can use the 4DISK.BAT (older versions may have only three disks) file to create a set of high-density (1.44Mb) installation diskettes. Use the following instructions to create the diskettes:
- Format four 3.5 inch, high-density diskettes and label them Installation Disk #1, #2, #3, and #4.
- Run 4DISK.BAT with the destination drive as its only parameter.
- In a DOS window, change to the folder that contains the installation files (make sure 4DISK.BAT is there) and at the command line type:
Or from the Start menu, you can use the Run dialog box if you specify a path.4DISK A:- Press Enter. The system prompts you to insert a blank 3.5 inch high-density diskette.
- Insert Installation Disk #1 and follow the on-screen instructions. The system prompts you for the remaining diskettes.
- After copying the installation files, write-protect the diskettes.
You can use these diskettes to install Command AntiVirus. To install the program:
- Insert Installation Disk #1 into Drive A.
- From the Start menu choose Run and type: A:SETUP
- Press Enter.
- Follow the screen instructions to complete the installation of the program.
 |
NOTE: If you ever need to run Command AntiVirus directly from a diskette, Installation Disk #1 contains all of the files necessary to do so. You can run Command AntiVirus from that diskette by running the file, F-PROT.EXE. |
You can find SCAN.BAT in the self-extracting file, SE_SCAN.EXE, which is on Command AntiVirus installation diskettes. SCAN.BAT performs a DOS-based scan that allows you to send the scan or program-related information to a log file. The log file is located on the local drive. When you run SCAN.BAT, it calls on two files, FPROT.BAT and ERR-CHK.BAT.
Before running SCAN.BAT, you must create or modify the LOGIN script environment variables shown below, using the appropriate values:
[sample LOGIN script] dos set NETNAME="FULL_NAME" name assigned by SYSCON dos set STATION="STATION" connection number at file server dos set NODE="P_STATION" node address
FPROT.BAT copies these values into the file, LOGG, which is located on the local hard drive. You will need to modify the path in FPROT.BAT to reflect where the report will be saved on the server. LOGG is later appended to the network report generated by F-PROT.EXE.
To use SCAN.BAT, change to the directory containing this batch file and run the following command:SCAN
There are several programs on the Command Software Systems BBS and FTP site that you can use with batch files to create automated scans. The file TIME_COM.ZIP contains files that allow you to check for seconds, minutes, hours, days, a specific day of the week, month, and year. For example, one of these files, DOW.COM (Day Of the Week), was used to create the ONEWEEK.BAT file shown below, which scans once a week.
@ECHO OFF REM ONEWEEK.BAT - WRITTEN BY CSS SPBPJN 9-27-94 REM TECHNICAL SUPPORT DEPARTMENT REM This file is designed to only execute a series REM of commands when a particular day is reached. REM Only one day is used, therefore, only one day REM out of the week can be specified. REM NEEDED FILE:DOW.COM > RETURNS ERRORLEVEL 0 TO 6 REM THE CORRESPONDING NUMBERS FOR THE DAYS OF THE REM WEEK ARE: SUN = 0, MON = 1, TUES =2, WED =3, REM THURS = 4, FRI = 5, SAT =6 REM PLACE THE NUMBER FOR THE DAY OF WEE* YOU WANT REM F-PROT TO RUN ON AFTER "SET DAY_TEMP=" LINE REM CURRENTLY,F-PROT IS SET TO EXECUTE ON MONDAY. SET DAY_TEMP=1 :DAYWEEK DOW.COM FOR %%V IN ( 0 1 2 3 4 5 6 ) DO IF ERRORLEVEL %%V SET OW_TEMP=%%V IF %OW_TEMP%==%DAY_TEMP% GOTO ACTION GOTO END :ACTION REM THIS IS WHERE YOU WANT TO INSERT THE DESIRED REM STATEMENTS THAT WILL RUN ON THE DAY SPECIFIED. REM BELOW IS A SAMPLE LINE FOR THE F-PROT STATEMENT REM TO BE INCLUDED WHICH YOU MAY WANT TO CHANGE. YOU REM CAN ALSO ADD STATEMENTS BEFORE AND AFTER THE REM F-PROT LINE FOR ITEMS THAT YOU WANT TO OCCUR REM ON THE SAME DAY. ECHO SCAN BEING PERFORMED C:\F-PROT\F-PROT.EXE /HARD /DISINF GOTO END :END REM CLEAR OUT VARIABLES FOR %%V IN ( DAY_TEMP OW_TEMP ) DO SET %%V=
Command AntiVirus provides several utilities for working with VIRSTOP. You can use these utilities for automating the distribution of upgrades.
This utility confirms the loading of a broadcast TSR. B-CHECK provides one of four return codes that you can use with a batch file. The following table contains descriptions of these return codes:
B-CHECK RETURN CODES
Return Code Description 0 NOVCAST or BANCAST is installed. 1 NOVCAST or BANCAST is not installed. Be sure to copy the proper files to the directory. 2 The version of NOVCAST or BANCAST is older than expected. Be sure to copy the proper updated files to the directory, then restart the computer. 3 The version of NOVCAST or BANCAST is newer than expected. Various versions of NOVCAST or BANCAST are being loaded. Display a specific warning message.
REBOOT.COM forces a restart of a workstation after updating a user's version of Command AntiVirus and VIRSTOP. You can include REBOOT.COM as the last statement in UPDATE.BAT.
You can broadcast notification of a virus detected by VIRSTOP over NetWare and Banyan Vines networks. For more information, refer to Novell NetWare Broadcasting and Banyan Vines Broadcasting.
V-CHECK.COM provides one of four return codes that you can use with a batch file. The following table contains descriptions of these return codes:
V-CHECK RETURN CODES
Return Code Description 0 VIRSTOP is installed. 1 VIRSTOP is not installed. Be sure to copy the proper files to the directory. 2 The version of VIRSTOP is older than expected. Be sure to copy the proper updated files to the directory, then restart the computer. 3 The version of VIRSTOP is newer than expected. Various versions of VIRSTOP are being loaded. Display a specific warning message.
F-TEST.COM is a utility, located in the F-PROT directory, that you can use to test the effectiveness of VIRSTOP.EXE. Run this utility from the command line to ensure that VIRSTOP.EXE is loaded and functioning properly. When you run F-TEST, the system displays the following message:
VIRSTOP is installed and active
If F-TEST.COM reports that VIRSTOP.EXE is not functioning properly, you may need to change the order in which VIRSTOP.EXE is loaded into memory.
 |
F-TEST does not show VIRSTOP active if you run F-TEST from a DOS shell under Windows. This process takes place because Windows has an int 21 handler that intercepts requests before VIRSTOP. |
We have also included the file, SE_EICAR.EXE, on your distribution diskettes. When you run this file, a test file, EICAR.COM (from European Institute for Computer Anti-Virus Research), is extracted from it.
The purpose of the EICAR test file is to provide an industry standard solution to test anti-virus products. The EICAR test file is the result of a cooperative effort between various anti-virus researchers. You can use this test file to safely:
- Verify that your anti-virus protection is installed properly
- Verify that real-time protection is active
- Demonstrate what happens when a virus is found
- Test custom messages that you create
To test a manual scan you can either copy EICAR.COM to your hard drive and run a scan or you can leave EICAR.COM on a diskette and scan the diskette.
To test the real-time protection of either DVP or VIRSTOP, run or copy EICAR.COM.
If Command AntiVirus is installed properly and real-time protection is active, the system displays a message box indicating that EICAR test virus has been found.
If the program is not installed properly or real-time protection is not active, the system displays the following message:
"EICAR-STANDARD-ANTIVIRUS-TEST-FILE!"
NOVCAST.EXE is a TSR that provides network notification to specified users and groups of users. You can load NOVCAST in the user's AUTOEXEC.BAT start up file.
NOVCAST works in conjunction with VIRSTOP in DOS and WVIRSTOP in Windows. (WVIRSTOP is an alternative to the default real-time protection, DVP, in Windows.) To run NOVCAST you must first have VIRSTOP loaded. NOVCAST should be run after login so that the identity of the user who initiated the virus broadcast will be included in the broadcast.
The following table contains switches that you can use with NOVCAST:
NOVCAST Switches
Switches Description /USER=NAME Name the user who will be notified. /GROUP=NAME Name the group that will be notified. /QUIET Unload NOVCAST, if it was the last TSR loaded. /? Display options.
You can enter any combination of user and group names from the command line. NOVCAST notifies the first 10 users that you specify. For example:
NOVCAST /GROUP=SUPPORT /USER=SUPERVISOR
/GROUP=TECH /USER=PAT
At load-time, NOVCAST locates the names of the Support group and adds them to the list of persons who will be notified if an infected file or floppy disk is found. If there are still less than 10 users, Supervisor is added to this list.
 |
NOTE: If there are five members in the Support group and one Supervisor, the program notifies the first four members of the Tech group. If there are four members in the Tech group, the system will not notify the user, Pat, because the program only notifies 10 users. |
BANCAST.EXE provides network notification to specified users and groups of users. To run BANCAST you must first load VIRSTOP. Run BANCAST after login so that the identity of the user who initiated the virus broadcast will be included in the broadcast.
The following table contains switches that you can use with BANCAST:
BANCAST Switches
Switches Description /USER=NAME Name the user who will be notified. /GROUP=NAME Name the group that will be notified. /LOG Stores real-time alerts. /QUIET Suppresses any installation messages. /? Display options.
 |
NOTE: You should always provide the log name with a drive path to insure that each of the audit file entries is stored in the same place. Not using a drive/path can result in uses the following files: |
BANCAST Files
Program Description BANCAST.EXE This DOS TSR is responsible for notifying WVIRSTOP and calling VINESMSG. VINESMSG.EXE This module is called by BANCASTBANCASTrunning and WVIRSTOP when it is necessary to perform VINES broadcasting. VINESMSG.PIF This Windows program information file is used by VINESMSG to provide background notification. WVIRSTOP.EXE This Windows program intercepts notifications sent by BANCAST. WVIRSTOP.EXE displays an alert to the user and calls VINESMSG if needed.
Real-time programs provide an important level of protection. If limited memory is a factor, you may need to configure your system(s) differently than the default settings. For more information, refer to the Command AntiVirus in Windows chapter.
This TSR is the original, DOS-based, real-time scanning engine. VIRSTOP.EXE requires about 4K of conventional memory. You can customize VIRSTOP by using command-line switches or by making changes to VSCONFIG (located in the F-PROT directory). For more information, refer to the Command AntiVirus in DOS chapter.
This TSR is the broadcasting agent. When VIRSTOP comes across a virus, NOVCAST sends a warning to up to ten users on the network. NOVCAST requires slightly more than 2K of conventional memory.
This TSR provides notification to specified Banyan Vines groups and users. BANCAST is similar to NOVCAST.
This Windows component is a secondary option for real-time protection within Windows. When DVP is not used, WVIRSTOP.EXE allows VIRSTOP's notification messages to be displayed in a Windows dialog box.
Although VIRSTOP requires less than DVP, VIRSTOP uses a smaller set of virus signatures. Because of these limitations, VIRSTOP detects fewer viruses in comparison to DVP. For example, VIRSTOP does not detect any macro viruses.